The official website of Metasploit.com and its parent company rapid7.com has been hijacked and defaced today by Pro-Palestine Hackers with the handle ‘Kdms Team“.
Pro-Palestinian Hackers managed to trick Register.com, who manage the DNS records for metasploit.com, into believing that they were authorised to change them – redirecting anyone attempting to visit the Metasploit site to a different part of the net, under the hackers’ control.
Hacked Sites with Mirrors(Proof of Hack):
- http://www.rapid7.com
- http://www.metasploit.com
- http://kdmsteam.metasploit.com
- http://www.zone-h.org/mirror/id/20960363
- http://www.zone-h.org/mirror/id/20960364
- http://www.zone-h.org/mirror/id/20960367
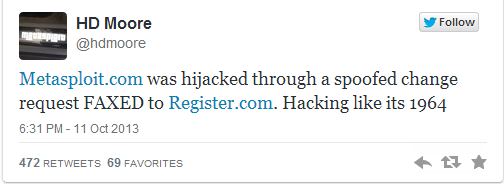
H D Moore, the Chief Research Officer of Rapid7 and Chief Architect of Metasploit confirmed that the website was hack via a spoofed DNS change request sent via fax to its registrar, Register.com.
Earlier this week, The hackers became popular by hijacking the official domains of Whatsapp, Avira Antivirus, AVG Antivirus, Redtube and Alexa.
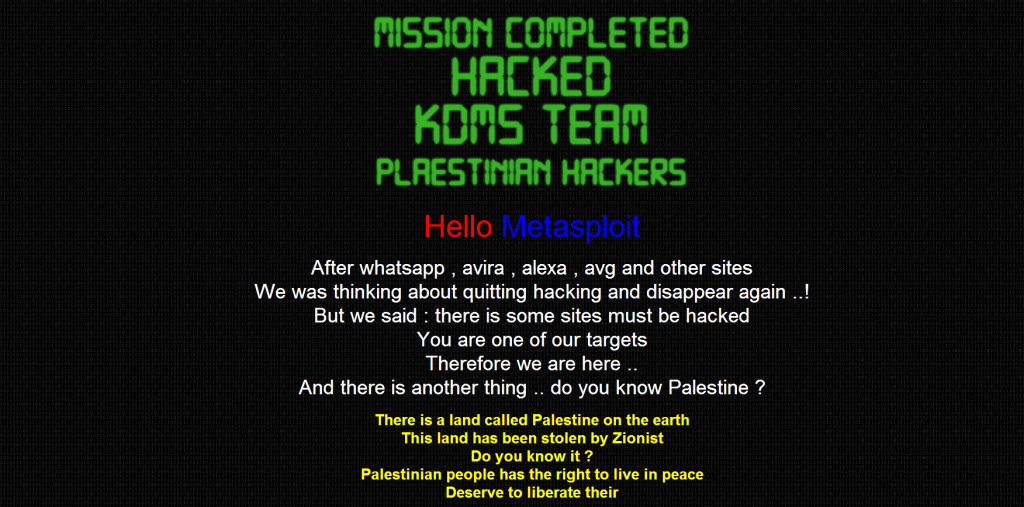
The Hackers wrote the following note on the deface page.
“Hello Metasploit. After whatsapp, avira, alexa, avg and other sites we was thinking about quitting hacking and disappear again! But we said: there is some sites must be hacked. You are one of our targets. Therefore we are here. There is another thing. Do you know Palestine? There is a land called Palestine on the earth. This land has been stolen by Zionist. Do you know it? Palestinian people has the right to live in peace Deserve to liberate their land and release all prisoners from israeli jails. We want peace. Long Live Palestine !
Rapid7 issues an official statement regarding the incident.
“This morning the DNS settings for Rapid7.com and Metasploit.com were changed by a malicious third-party. We have taken action to address the issue and both sites are now locked down. We are currently investigating the situation, but it looks like the domain was hijacked via a spoofed change request faxed to Register.com. We apologize for the service disruption, and do not anticipate any further implications for our users and customers at this time. We will keep everyone posted as we learn more, and let the community know if any action is needed.”