The NIC hacker hit domain registrar again and this time 1337 hacker hijack Google Malaysia official domains(www.google.com.my) with DNS poisoning attack. At the time of writing, Both of Google Malaysia official sites are defaced and showing the message left by the hackers.
Two days before, I wrote, If the domain registrar server or NIC of a country was hacked recently, there’s a decent chance it is hacked by Pakistani Hacker 1337. He proved it again.
Hacked Sites with Zone-h Mirrors:
- www.google.com.my
- www.google.my
- http://www.zone-h.com/mirror/id/20957809
- http://www.zone-h.com/mirror/id/20957806
See Also: Google Kenya & Google Burundi Hacked By 1337
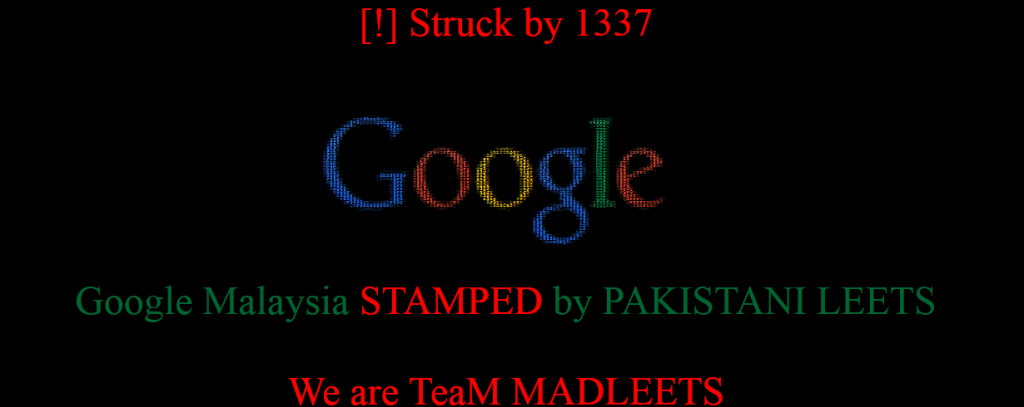
Google Malaysia domains are defaced with DNS poisoning attack. The hackers managed to hack into MYNIC (Malaysia Network Information Centre) and changed the authoritative DNS records of the domain, to point the domain name to the madleets name server. Currently, Website whois records shows the following name servers.
Primary Name Server: b0x4.madleets.com
Secondary Name Server: b0x3.madleets.com
There is no specific reason mentioned by the hacker on the deface page. The hacker writes on the deface page,
“Struck by 1337! Google Malaysia STAMPED by PAKISTANI LEETS! We are TeaM MADLEETS! Pakistan Zindabad”
All NIC’s or domain registrars that has been hacked by the 1337 hacker can be found here.
Update:
MYNIC site issued a statement and confirmed the attack and that it had been resolved pending propagation across the internet:
We can confirm there was unauthorised redirection of www.google.com.my and www.google.my to another IP address by a group which called themselves TeaM MADLEETS.
The problem was alerted in the early morning and MYNIC Computer Security Incident Response Team (CSIRT) immediately started to resolve the issue. The domain name www.google.com.my has been restored to their correct information at 7.10 am today and www.google.my is still resolving.

Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | TechCrunch()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337 | Modulates.com()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | LiMiT()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 « W 8 . M S()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337 - Indian Radios | Indian Radios()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Digital Tech +()
Pingback: IT Blog » Post Topic » Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337()
Pingback: Hackers bring down Google’s site in Malaysia | LiMiT()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | TechNewsDB()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 « DevelopersArena.com()
Pingback: Google Malaysia homepage falls victim to DNS attack | LiMiT()
Pingback: Hackers bring down Google's site in Malaysia - Daily Tech Whip | Daily Tech Whip()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | iyaan.info()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | TechRiddle()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Around the World()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Lead Generation Card()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337 | A Pressed World()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Tech Wire Daily()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | yvyfecanysu()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337 | Tuto Drupal News()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker … | Google()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | samanthamfu806()
Pingback: آیا هکرها واقعاً سایت گوگل مالزی را هک کردهاند؟()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets' Hacker 1337()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Leet Gazette()
Pingback: Yesterday, Google Malaysia domain was hijacked by ‘Team Madleets’ - Hackers News Bulletin()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By 'Team Madleets' Hacker ... - TechCrunch - Web Design Egypt()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By 'Team Madleets' Hacker ... - TechCrunch |()
Pingback: Google Malaysia Site DNS Hacked Oleh Hacker ‘Tim Madleets’ 1337 « indonesia-defacer.com()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Security Issues()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Blog()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker … - TechCrunch | TodayJournals.Com()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 - TechFatTechFat()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker … - TechCrunch | Big Daily News()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker … - TechCrunch | Everyday News Update()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By 'Team Madleets' Hacker ... - TechCrunch | Techbait Tech News()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker … - TechCrunch | Custom News Cast()
Pingback: Google Malaysia Site DNS Hacked | Google()
Pingback: آیا هکرها واقعاً سایت گوگل مالزی را هک کردهاند؟ - تالارهای گفتمان جی تاک()
Pingback: cloud web service()
Pingback: Google Malaysia Site DNS Hacked | Cyber security labs by Cipher Net AB()
Pingback: Google Malaysia Site DNS Hacked, Credit Claimed By ‘Team Madleets’ Hacker 1337 | Banking IT Solutions Architect | Enterprise Architecture()