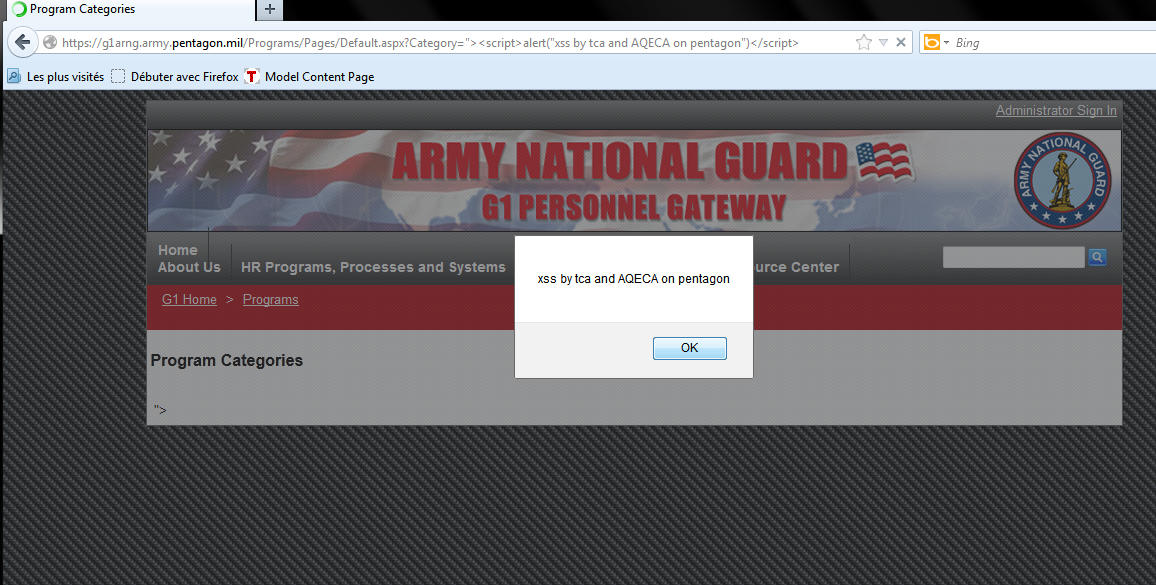
The hackers provided a screen shot to the The Hackers Post which shows the execution of vulnerability and POC (Proof of Concept).
[#] - Main Site Link:
https://g1arng.army.pentagon.mil/Pages/Default.aspx
[#] - Vulnerable Link:
https://g1arng.army.pentagon.mil/Programs/Pages/Default.aspx?Category=”>
[#] - Vulnerability Type:
XSS (Cross Site Scripting)
[#] - Status:
Not Fixed [Critical]
[#] - Tested on:
Firefox 18.0.1
Cross Site Scripting (also known as XSS or CSS) is generally believed to be one of the most common application layer hacking techniques. It is listed in Top 10 OWASP Vulnerability 2013. The Hackers Post written an article: A basic guide to XSS to get basic understanding of Cross Site Scripting.
According to HackRead, The hackers claimed to have assistance from Chinese hackers during their #opBlackSummer.
“Not only that we also have some important file we got after cookies stealing from the pentagon mail added to that there are some Chinese hackers who collaborate with us”.
This is not the first time Pentagon server vulnerable to XSS flaw; in past Anonymous hackers not only exploited XSS but many other vulenrabilities that led to breach of military server, leaking classified secret information online.
Its quite embarrassing that Pentagon website is vulnerable to the most common flaw, which exists in one of its sub domain. This left a question to the Pentagon web security team that such a common XSS flaw exists in their server.